After An Intrusion Has Occurred And The Intruder Has Been Removed From The System
After an intrusion has occurred and the intruder has been removed from the system. CHAPTER TWO LITERATURE REVIEW 21 SENSORSMOTION SENSORS Motion sensors are types of electronic security device that senses movement and usually triggers an alarm. Backs up all files with the archive bit set. If no intrusion signal is observed by the returning.
This should be fifteen minutes or less in most urban areas in the United States. The system detects unauthorized users attempting to enter into a computer system by comparing user behavior to a user profile detects events that indicate an unauthorized entry into the computer system notifies a control function about the unauthorized users and events that indicate unauthorized entry into the computer system and has a control function that automatically takes action in response to the event. The system includes a test mode operable from outside the protected premises to determine if the system has been tampered with by an intruder.
It has been determined that at midnight the system suddenly began deleting files. Next make sure you are using trusted media and programs notnecessarily your last backup to restore the system. A compromise of the host system might affect multiple servers.
Two weeks later employees report they cannot access files. Resets the archive bit. 457 1- After an intrusion has occurred and the intruder has been removed from the system which of the following is the best next step or action to take.
The original access time which could have been used as evidence is gone forever. LITERATURE REVIEW OF A BURGLAR ALARM SYSTEM. Answer 1 of 2.
After an intrusion has occurred and the intruder has been removed from the system which of the following is the best next step or action to take. Finally we must consider data that is stored on the hard drive but isnt accessible all the time. In the vast majority of cases the safe room only needs to be used for the short period of time it takes for the police to arrive at your home after they have been called.
Many types of motion sensors can sense motion in total darkness without an intruder becoming aware that an alarm has been triggered. Whenyou reinstall the operating system you will attempt to write over thebad parts and the problem will suddenly become apparent.
It has been determined that at midnight the system suddenly began deleting files.
After an intrusion has occurred and the intruder has been removed from the system which of the following is the best next step or action to take. After an intrusion has occurred and the intruder has been removed from the system which of the following is the best next step or action to take. The system includes a test mode operable from outside the protected premises to determine if the system has been tampered with by an intruder. Which of the following are disadvantages to server virtualization. If you do so then you are intruding in someones behav. Emphasis should be placed on the word temporary. Back up all logs and audits regarding the incident. This should be fifteen minutes or less in most urban areas in the United States. For instance a disk may have bad spots that are in unused files.
Two weeks later employees report they cannot access files. CHAPTER TWO LITERATURE REVIEW 21 SENSORSMOTION SENSORS Motion sensors are types of electronic security device that senses movement and usually triggers an alarm. This will significantly increase your time to recover. It has been determined that at midnight the system suddenly began deleting files. Which of the following are disadvantages to server virtualization. This should be fifteen minutes or less in most urban areas in the United States. The system detects unauthorized users attempting to enter into a computer system by comparing user behavior to a user profile detects events that indicate an unauthorized entry into the computer system notifies a control function about the unauthorized users and events that indicate unauthorized entry into the computer system and has a control function that automatically takes action in response to the event.



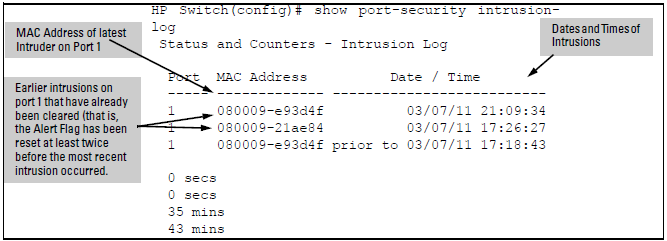







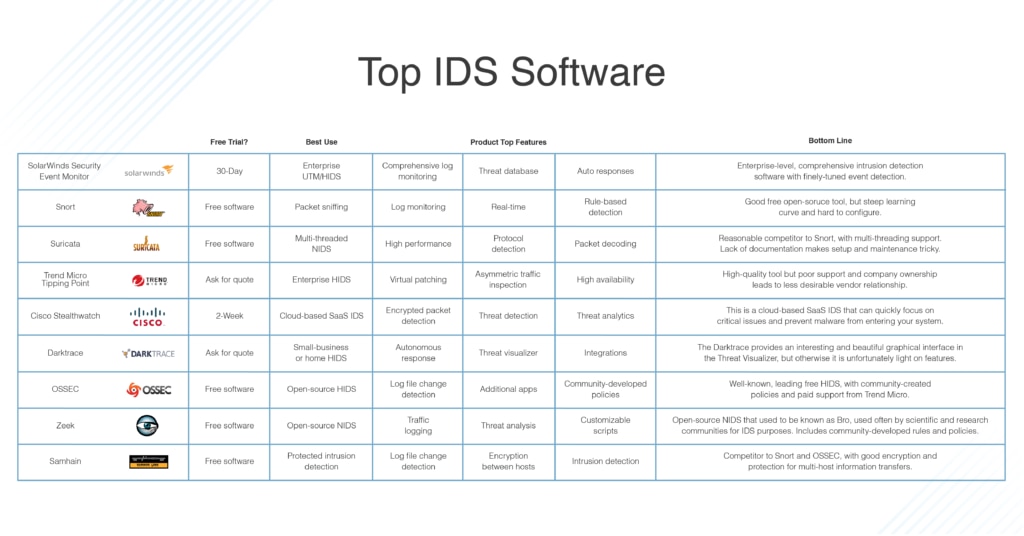







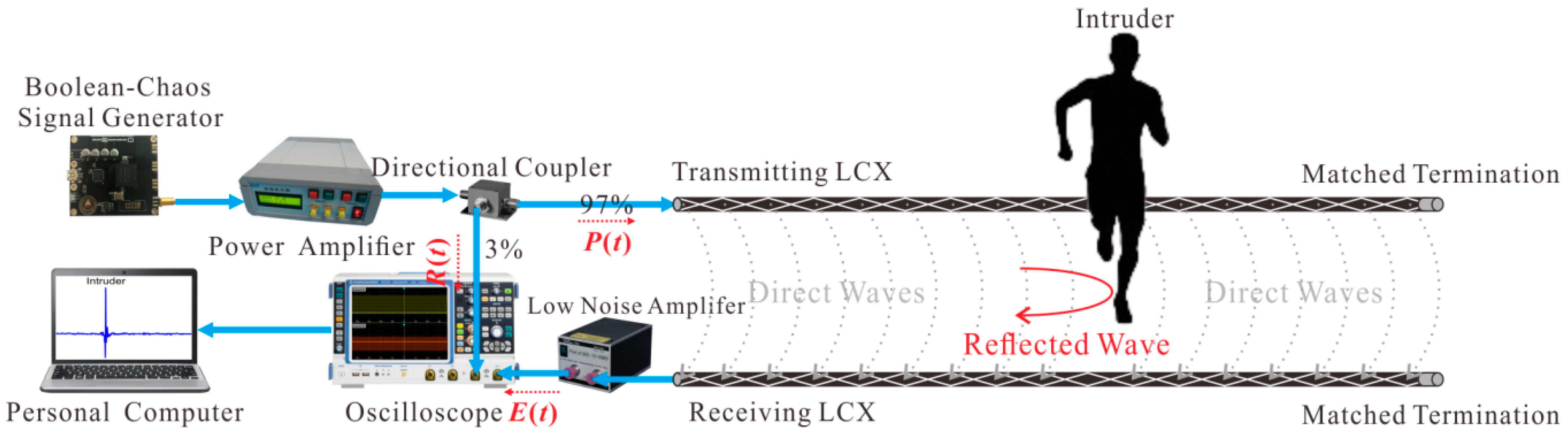
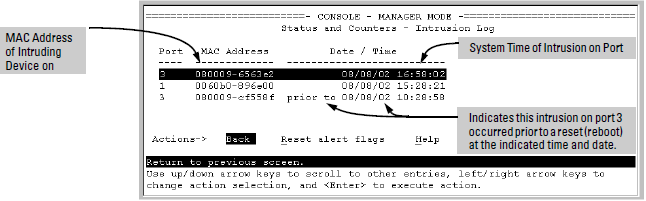

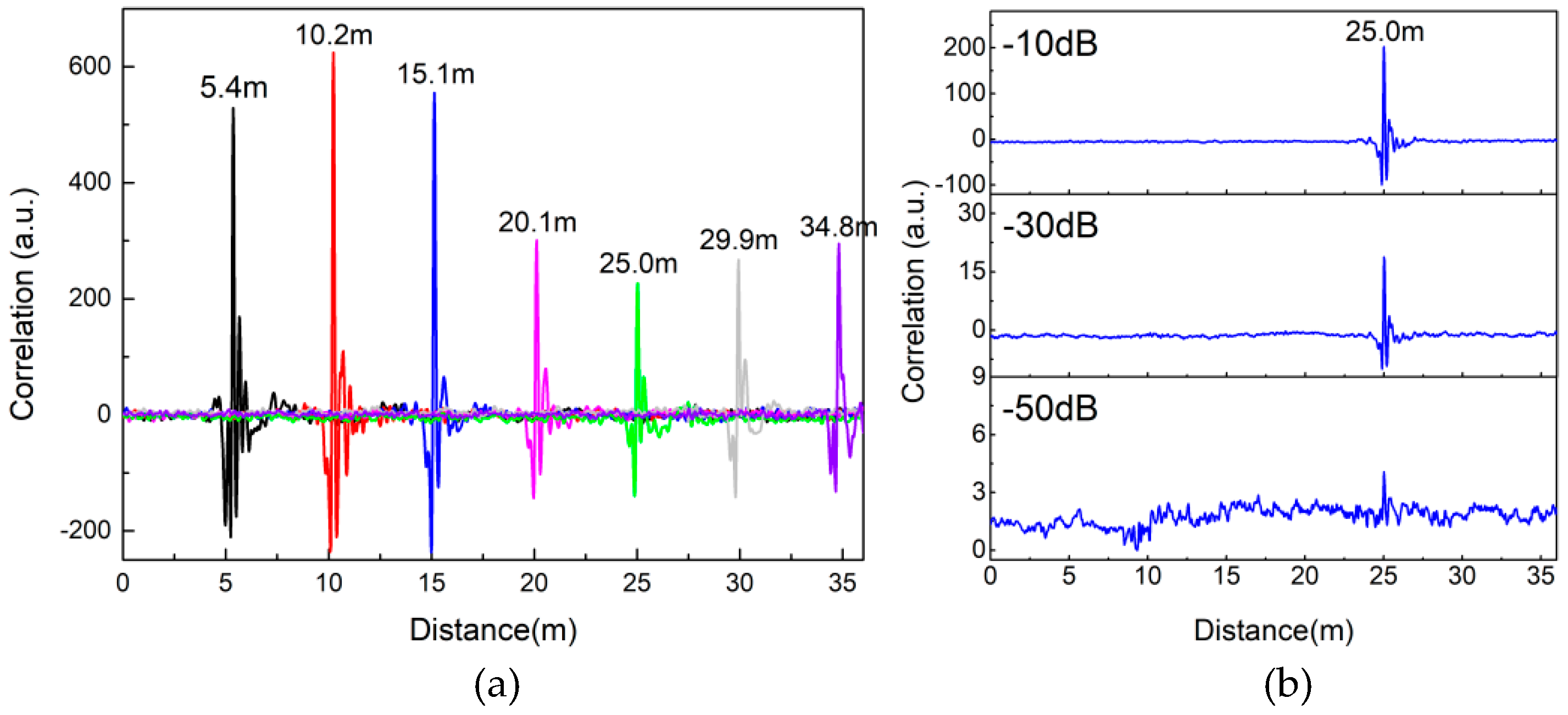
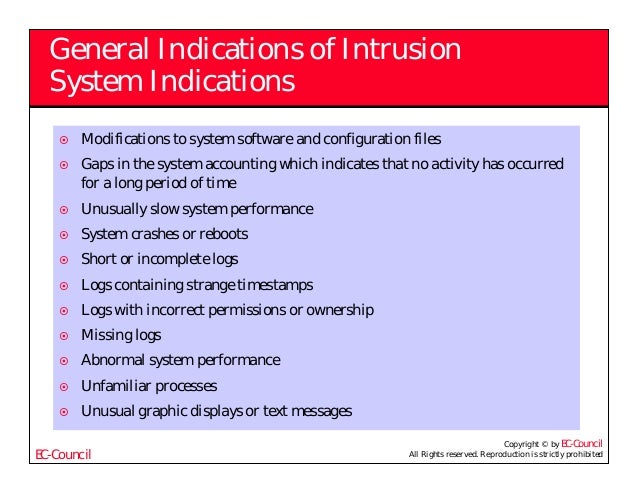
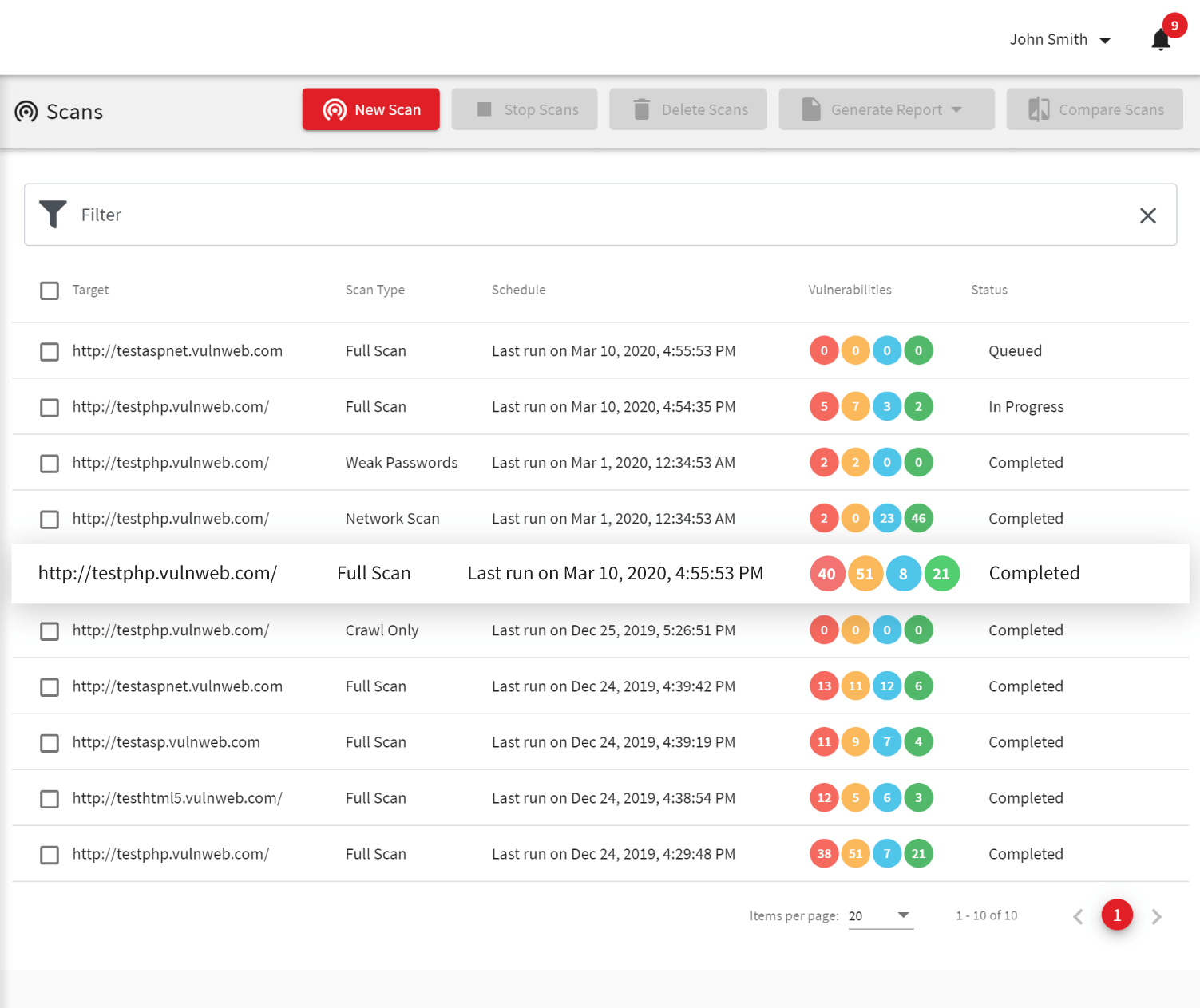

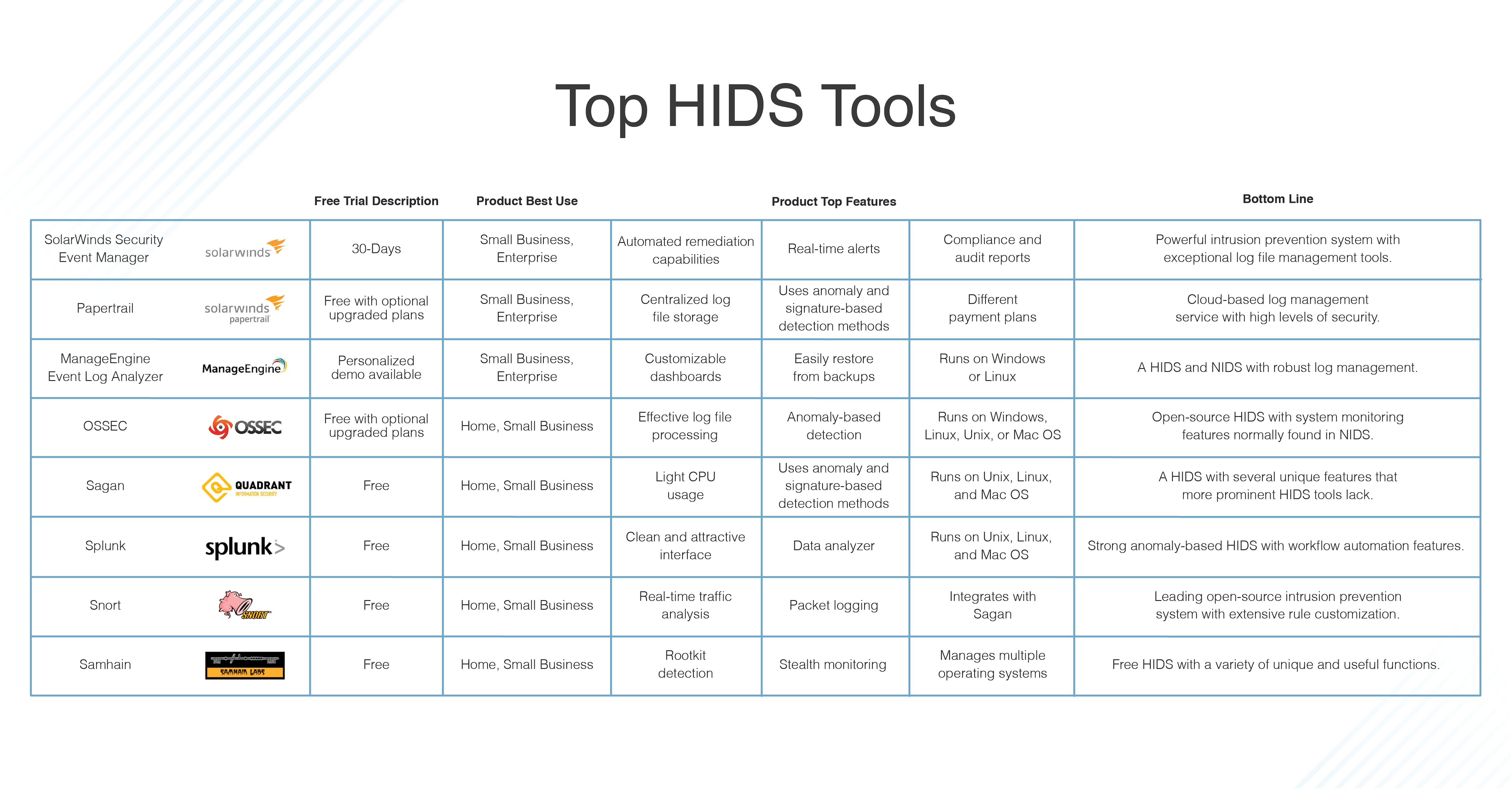

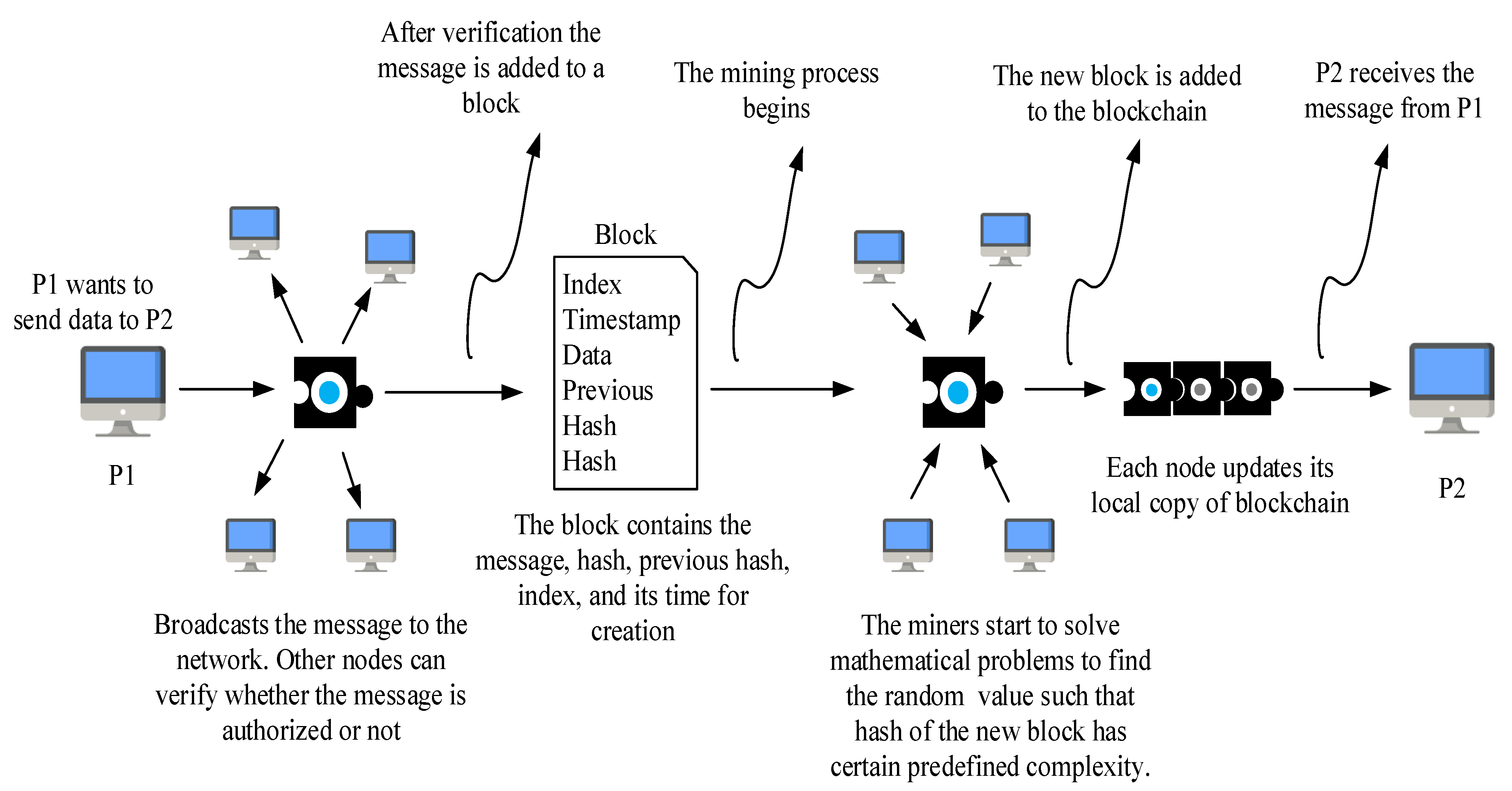
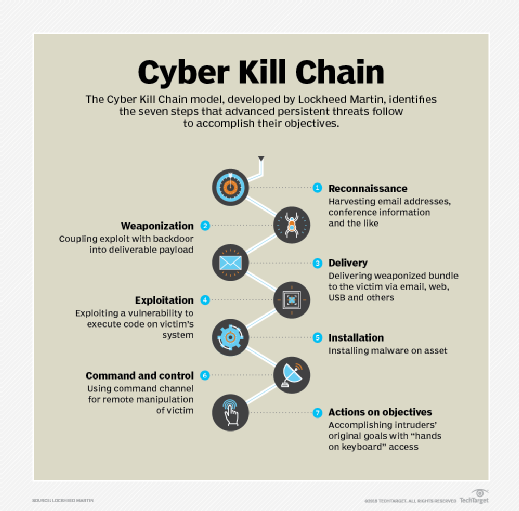


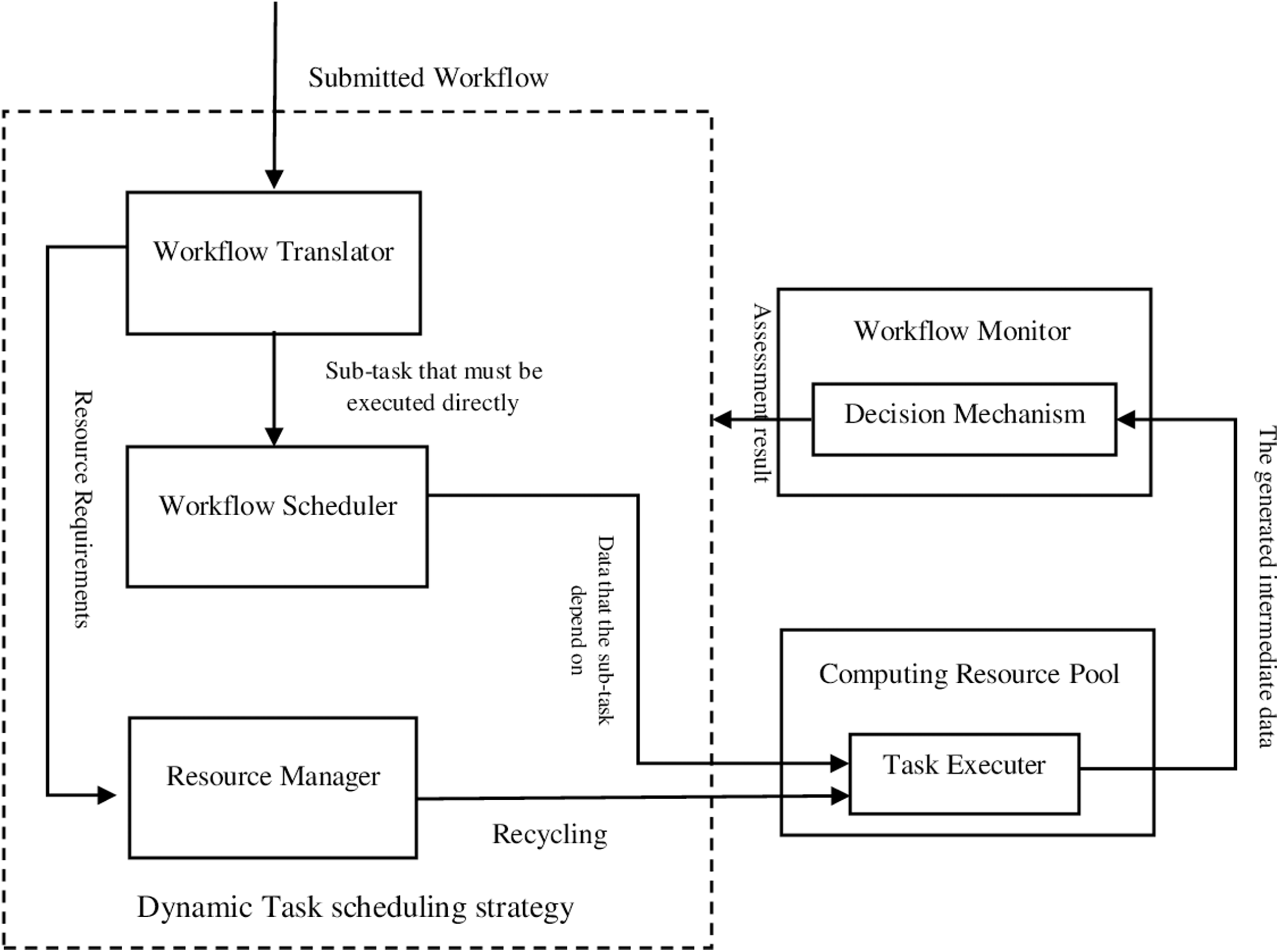
Post a Comment for "After An Intrusion Has Occurred And The Intruder Has Been Removed From The System"